Most Companies Don’t See Strategic Threats Coming Until It Is Too Late – Part 3

 Strategic threats are emerging more quickly and in increased numbers than at any time in our history. There is a reason for that. We operate business in an interconnected global economy and marketplace that is always on, continuously changing and is hyper-competitive. As such, the strategic planning discipline is now being called upon to be the lookout watchtower that business organizations must rely upon to surveil environmental conditions, then proactively work to mitigate damage to organizational assets before it can occur. This requirement is forcing organizations to shift to increasingly effective strategic planning and strategy execution methods. This article, the final segment of the series, discusses: threats, risks and vulnerabilities. Lastly, the article provides a framework for strategic threat management that can and should be incorporated into the planning discipline of any organization.
Strategic threats are emerging more quickly and in increased numbers than at any time in our history. There is a reason for that. We operate business in an interconnected global economy and marketplace that is always on, continuously changing and is hyper-competitive. As such, the strategic planning discipline is now being called upon to be the lookout watchtower that business organizations must rely upon to surveil environmental conditions, then proactively work to mitigate damage to organizational assets before it can occur. This requirement is forcing organizations to shift to increasingly effective strategic planning and strategy execution methods. This article, the final segment of the series, discusses: threats, risks and vulnerabilities. Lastly, the article provides a framework for strategic threat management that can and should be incorporated into the planning discipline of any organization.
Is It a Risk or a Threat?
If you were asked to describe the difference between a risk and a threat, how would you define the divergence in meaning? Though the terms “risk” and “threat” are often used interchangeably, they are not the same.
Are the following risks or threats?:
- Increasing industry regulation and compliance standards: risk or threat?
- Rising levels of government debt that may have a strong impact on the cost of credit in future: risk or threat?
- Commodity price inflation and pressure from low-cost competitors: risk or threat?
Perhaps it was a trick question, but the statements were all forms of threats. Now let’s look at the associated risks for each one.
- Regulation and compliance standards: The risk would be that regulation will add costs, stall business decision making and make planning more difficult.
- Rising levels of government debt that may have a strong impact on the cost of credit in future: The risk is reduced access to credit.
- Commodity price inflation and pressure from low-cost competitors: The risk is cost cutting to keep from losing market share from less expensive competitors.
So how did you do? Were any of the statements tricky? Most organizations struggle with risk and threat identification, therefore the management of these areas is usually lacking.
Identification of Threats
Threats are usually associated with conditions in the environment, but could also arise from specific antagonistic actions. A strategic threat is any significant aspect of the external environment that can negatively effect the organization and potentially undermine the strategy and strategic vision.
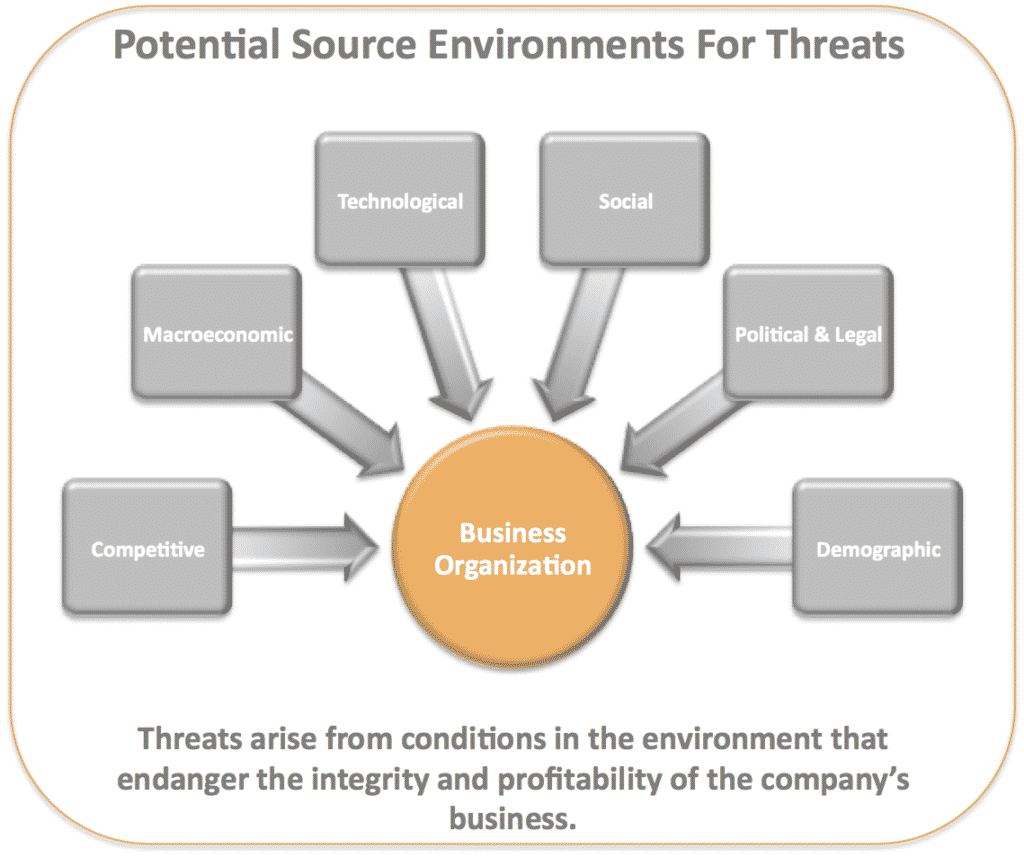
Strategic threats can be identified through environmental scans that explore factors in each of the major environmental regions that serve as the most common sources of business threats.
This graphic below summarizes these major sources of threats.
For instance, the globalization of production and markets may pose both an opportunity and a threat to a manufacturer. The opportunity being the lower barriers to cross-border trade as well as the likely ease of foreign investment. A threat might be the national differences in cost and quality factors in production. On the flip-side, the lower barriers to entry could also pose a threat, if competitors seek to mimic the manufacturer’s moves. This could lead to intensified rivalry.
Strategic threats arise because of change. For example, markets and technology are continuously in flux. Distribution channels change over time, as do social trends that may decrease or kill demand for old products and services.
Strategic threats unless recognized, guarded against and countered can result in significant negative outcomes for the organization.
Identification of Risks
Risks are about events that, when triggered, cause problems. Hence, risk identification can start with the source of problems, or with the problem itself. Remember, risks emanate from threats, but the manifestations are much broader and may be internal or external to the organization. For example, if a programmer working in a financial institution accidentally creates a security hole in a software application that transfers money between accounts, the mistake has introduced risk (the risk that money could be stolen from an account and transferred elsewhere undetected). If a person outside the business were to use the security hole, it would be a threat. The same is true if the programmer created the security hole on purpose.
Risks are related to the identified threats from SWOT analysis, so that is a valid reference to tap during the risk identification process. When either the source or problem is known, the events that a source may trigger or the events that can lead to a problem can be investigated. For example: banks withdrawing funding support for expansion; confidential information may be stolen by employees; weather delaying construction projects, etc.
Additionally, other methods of risk identification may be applied, dependent upon culture, industry practice and compliance. For instance, objectives-based risk identification can focus on any potential threats to achieving strategic objectives. Any event that may endanger achieving an objective partly or completely can be identified as risk.
Scenario-based risk identification is another method. In scenario analysis, different scenarios are created. The scenarios may be the alternative ways to achieve an objective, or an analysis of the interaction of forces in, for example, a market or battle. Any event that triggers an undesired scenario alternative is identified as risk.
As a final example, a taxonomy-based risk identification can be utilized, where the taxonomy is a breakdown of possible risk sources. Based on the taxonomy and knowledge of best practices, a questionnaire can be compiled and the answers to the questions used to reveal risks.
Modernizing the Strategic Planning Process
Just as a detective solving a crime looks for opportunity and motive with a suspect, strategic planners must look for threats in the environment based on a set of criterion and attempt to solve the exposure ahead of it occurring. Modernizing strategic planning most definitely involves a renewed approach to threat management and one that is more far-reaching than SWOT analysis and integrates better with strategic planning and execution.
For instance, threat management must address two dimensions of organizational strategy. It must protect the organization today (current-state) and it must also be forward-looking to serve as protection for the future strategic vision that the strategy prescribes and the strategic plan details.
Intention, Capacity and Opportunity
As we have covered thus far, threats are based on intention, capacity and opportunity to do harm to assets, in this case the organization or some facet(s) of the business. Therefore, protecting against threats is based on awareness, available resources and exposure.
Threats may not be always be malicious in the traditional sense. A regulatory authority is merely fulfilling its charter when it seeks to impose civil or legal actions against a company in violation of statutes. Likewise, a competitor seeking to take away another company’s market share is only doing what they should be doing to survive.
Modern strategic planning must therefore maximize the awareness of threats and optimize the deployment of available resources to combat threats based on prioritized exposures the organization faces.
Surviving and Thriving Through Threats
One approach to dealing with threats is to turn them into a competitive advantage instead of treating them as an afterthought. Superiority in threat management over a competitor can be a distinct strategic advantage. Therefore, planning for threats and managing them as they come up on the horizon can help a business to do better than just survive. It can literally help a business thrive in an environment filled with potential threats.
So how to we defend against threats – known and unknown? Since organizations cannot conceive of all threats in order to protect against them, the best solution is to protect against known threats and then focus remaining energies on managing risks and vulnerabilities.
Understanding Vulnerabilities and Risk
The business enterprise is an asset to be protected. The larger the organization, the more complex it can be to protect the asset.
It is the lack of asset protection affected by threats that leads to vulnerabilities and vulnerabilities lead to risk.
Risks are based on probability of occurrence and the consequence or cost incurred in the event the risk comes to fruition. Given that, organizations must identify risks and then do their best to estimate them in terms of cost of consequence. Once that has been done, high risks must be addressed by identifying counter-measures and performing them accordingly.
All risk can never be removed from a strategic plan, therefore business planning teams must approach risk from a cost / benefit perspective. Risk mitigation in planning can cost money and speed, but if risks are addressed early the organization can avoid future impediments.
The lesson? We cannot eliminate all threats, but can reduce risk by lowering vulnerability.
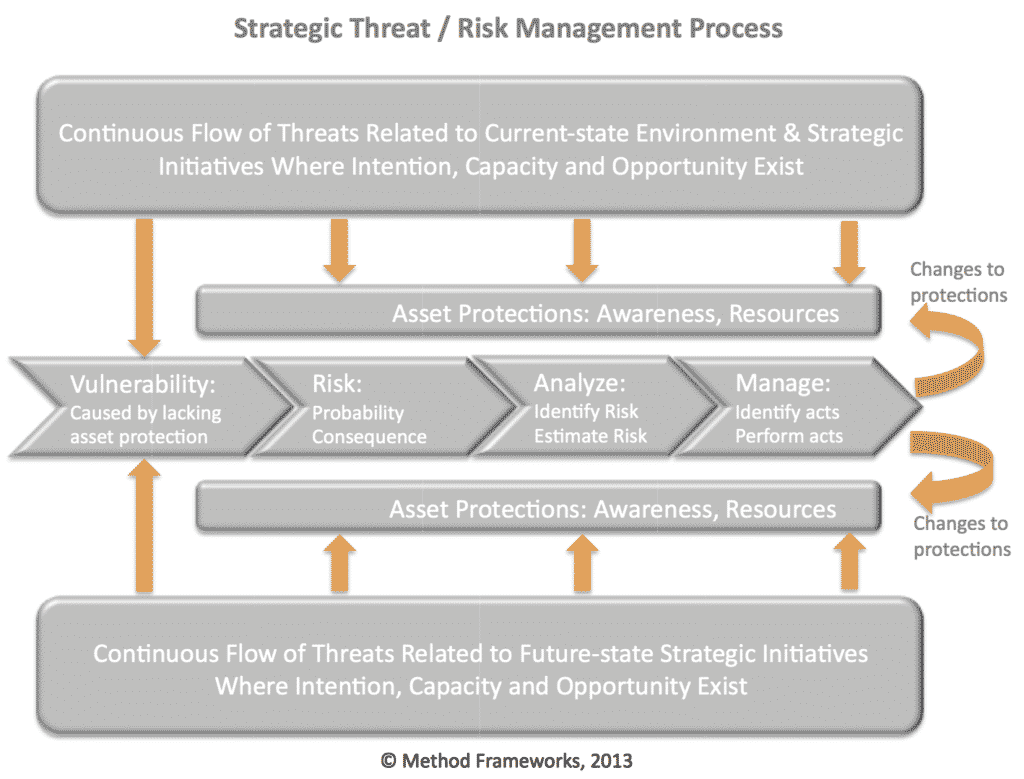
A Strategic Threat and Risk Management Framework
Threats will continuously flow into the business ecosystem, but not all threats pose a risk to the organization (the asset).
A strategic threat management framework must first determine what the threat or risk might potentially affect (people, property, and information, etc.). It is then prudent to examine the vulnerabilities and estimate the impacts the risk imposes. Actions can then be formulated to address the required protections.
The following are components of a Threat and Risk Management Framework:
Threat: Anything that can exploit a vulnerability, intentionally or accidentally, and obtain, damage, or destroy an asset.
Vulnerability: A vulnerability is a weakness or gap in our protection efforts.
Risk: Risk is the potential for loss, damage or destruction of an asset as a result of a threat exploiting a vulnerability. Risk can be thought of as the intersection of assets, threats, and vulnerabilities. Risk is a function of threats exploiting vulnerabilities to obtain, damage or destroy assets.
A mathematical representation of this relationship might be: Risk = Threat x Vulnerability x Asset.
Protections: The awareness of threats and risks as well as the application of organizational resources to prevent them from occurring.
A model for managing threats and risks must therefore take into account that threats (actual, conceptual, or inherent) may exist, but if there are no vulnerabilities then there is little or no risk. Similarly, a business can have a vulnerability, but if there are no related threats, then there is little or no risk.
The following framework demonstrates this point and can serve as a model to be incorporated into the strategic planning framework of an organization.
Surviving Threats
A sound strategy, robust strategic planning process and management discipline are the keys to business survival. Businesses will always face threats. They may come in the form of cheaper imports available from a foreign market, new legislation that forces business model changes or game-changing disruptive technologies that alter the buying trends of a core market. Long-term survival is dependent on environmental surveillance connected to good strategic planning and the protections that are put in place to safeguard against damage to organizational assets.
Change happens and successful businesses adapt and prosper. Winning businesses have incorporated forward-looking planning combined with operational execution that is dialed-in to key metrics attenuated to their strategic objectives. Strategic planning that includes environmental threat surveillance helps any business to navigate choppy waters, plan accordingly and signal the alarm when plans are no longer working.
***
> Read Part 1 of this series – “Most Companies Don’t See Strategic Threats Coming Until It Is Too Late – Part 1 of 3”
> Read Part 2 of this series – “Most Companies Don’t See Strategic Threats Coming Until It Is Too Late – Part 2 of 3”
Category : Business Operations